The vulnerability enabled an attacker, armed only with minimal information such as a victim’s last name and ZIP code, email address, phone number, or license plate, to perform the following actions:
- Control Vehicles Remotely: Start, stop, lock, unlock, and retrieve the current location of any vehicle.
- Access Location Data: Retrieve an entire year’s location history for any vehicle, accurate to within 5 meters and updated each time the engine started.
- Obtain Personal Information: Query and retrieve personally identifiable information (PII) for any customer, including emergency contacts, authorized users, physical address, billing details (e.g., the last four digits of a credit card), and vehicle PIN.
- Access Miscellaneous Data: Retrieve support call history, previous ownership records, odometer readings, sales history, and other sensitive information.
After reporting the vulnerability to Subaru, the affected system was patched within 24 hours, and no evidence of malicious exploitation was found.
Proof of Concept
The team demonstrated how they could take over a Subaru vehicle using only the license plate within approximately 10 seconds. They also retrieved over a year’s worth of location history from the vehicle.
Example:
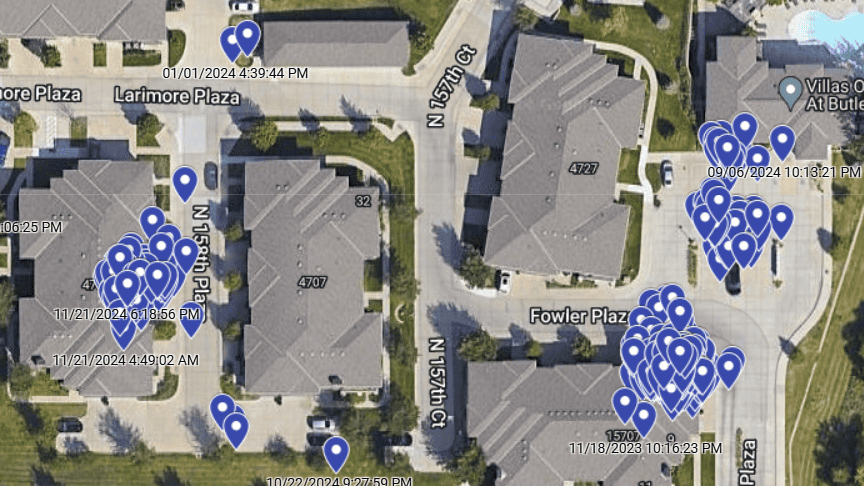
A map displayed 1,600 leaked coordinates from a 2023 Subaru Impreza. Similar data was accessible for any internet-connected Subaru.
Discovery Process
Sam Curry, having purchased a 2023 Subaru Impreza for his mother, decided to investigate its security vulnerabilities after spending years identifying flaws in other automakers’ systems. During a Thanksgiving visit to his mother’s home, he gained access to her account for testing purposes.
Auditing the MySubaru App
Curry began with Subaru’s MySubaru mobile app, which allowed users to send vehicle commands. He proxied the app using Burp Suite to intercept telematic command requests but found that its authorization mechanisms were robust and secure. After concluding that this approach was ineffective, he shifted focus to Subaru-related websites, suspecting employee-facing applications might have weaker safeguards.
Discovery of the Subaru Admin Panel
Curry reached out to Shah for assistance. Together, they identified a domain (subarucs.com) linked to Subaru’s infrastructure. A scan revealed the STARLINK Admin Portal (portal.prod.subarucs.com), which appeared to be an employee-facing system with administrative capabilities.
Exploiting the Admin Panel
Upon examining JavaScript files from the admin panel, Curry and Shah discovered an endpoint (resetPassword.json) that allowed password resets for employee accounts without requiring a confirmation token. They enumerated employee email addresses using another endpoint (getSecurityQuestion.json), validated one of them, and successfully reset the password to gain access.
Bypassing 2FA
Although the admin panel implemented two-factor authentication (2FA), it was circumvented by disabling the client-side overlay in the UI. Once inside, Curry and Shah accessed sensitive functionality, including the Last Known Location endpoint, which provided exact coordinates of a vehicle’s activity over the past year.
Demonstration and Additional Findings
The pair demonstrated the vulnerability by tracking Curry’s mother’s vehicle and later adding themselves as authorized users on a friend’s Subaru. They confirmed that the STARLINK admin panel granted full control over vehicles without notifying customers. Their friend received no alerts when her car was unlocked remotely.
Other endpoints exposed in the admin panel included tools to:
- Retrieve sensitive customer details (e.g., address, phone number, billing info).
- Grant or modify access to vehicles using minimal information.
Timeline
November 20, 2024: Vulnerability discovered.
November 21, 2024: Subaru patched the system, mitigating the issue before it was exploited maliciously.
This case underscored the importance of rigorous security testing for connected vehicle systems and highlighted the potential risks of centralized administrative systems in the automotive industry.
Read Sam Curry’s story at https://samcurry.net/hacking-subaru
Video: https://youtu.be/0i8juy6RPBI?feature=shared