N o one wants their cars to be hacked especially automakers. Cars have thousands of ECUs an computer systems that all connect to each other. Then cars can connect to cloud through telematics systems or smartphones. Every where there is a connection there can be a new place to hack into the car and take over. This year for AUTO Connected Car News’ Tech Car Awards the following companies have been nominated for the Best Automotive Cyber Security Solution. Here are details about the products so that you can be better informed when you vote.
o one wants their cars to be hacked especially automakers. Cars have thousands of ECUs an computer systems that all connect to each other. Then cars can connect to cloud through telematics systems or smartphones. Every where there is a connection there can be a new place to hack into the car and take over. This year for AUTO Connected Car News’ Tech Car Awards the following companies have been nominated for the Best Automotive Cyber Security Solution. Here are details about the products so that you can be better informed when you vote.
Keeping the CAN Bus as Safe as it Can be Karamba Security’s SafeCAN
Karamba Security’s SafeCAN is security software that seamlessly protects automotive networks from hacking by authenticating in-vehicle communications with zero network overhead.
Carmakers have been demanding authenticated in-car communications to protect vehicles against malicious messages sent by unauthorized Electronic Control Units (ECUs) or via third-party dongles. Such prevention is essential in light of dongles commonly provided by insurance companies to monitor driver behavior and offer discounted premiums to responsible drivers. Car companies can’t control the data exchange generated by those dongles, creating a new attack vector. A Toyota car model was compromised by researchers through a dongle from Progressive Insurance, for example.
Solving this problem is made even more difficult because in-car networks, and especially the CAN bus, are saturated and cannot add authentication data, which consumes network throughput. The resulting lack of in-car authentication leaves the car’s safety systems exposed to malicious commands sent due to such dongle-based attacks or hacked over-the-air (OTA) in-vehicle updates.
SafeCAN is the automotive industry’s first cybersecurity solution to offer in-vehicle network authentication with zero network overhead. It can be implemented without overtaxing the car’s internal communications to protect and authenticate CAN bus communications.
Karamba’s latest software product enables automobile manufacturers to seamlessly harden the networks to secure the car’s safety systems. There is no need to change network protocols, or add any additional network packets to ensure the authenticity of source-destination authentication and overall in-vehicle network authentication.
By offering seamless encryption for ECU communication, SafeCAN hardens the network leading to and from the car’s safety systems and ensures that only legitimate commands are received by the car’s safety systems. Commands originating from invalid sources are ignored.
In addition to hardening the car networks against physical attacks, SafeCAN enables secure OTA updates from the cloud to any ECU in the car. OTA products use secure channels from the OEM cloud to the primary ECU, which serves as the OTA’s entry point in the car. However, due to lack of network authentication, attackers may hack the car, impersonate an OTA update and deploy malicious software on safety ECUs. By hardening the network between the OTA primary ECU to the in-vehicle safety systems, target ECUs will not accept changes, unless it was authenticated by SafeCAN.
This marks the first time that any vendor has offered end-to-end network safety in a pragmatic way that overcomes industry barriers.
SafeCAN helps automakers and tier-1 providers meet their security goals and comply with regulations such as those set out in the United States by the National Highway Traffic Safety Administration (NHTSA) and U.S. Department of Transportation (DOT)’s newly published federal guidance, Automated Driving Systems (ADS): A Vision for Safety 2.0, as well as the guidelines defined in the SELF DRIVE Act passed by the U.S. House of Representatives. Similar guidelines are emerging worldwide.
SafeCAN complements and extends Karamba’s Autonomous Security Carwall product to provide end-to-end in-vehicle security. Carwall hardens externally-connected ECUs by sealing their binaries according to factory settings. This prevents cyberattacks and in-memory attacks from compromising the car ECU’s, while eliminating false positives that risk consumers’ safety.
Together, SafeCAN and Carwall assure car safety by blocking hackers at the gate and by providing secure in-car traffic and authenticated OTA updates.
Kaspersky’s SCU
Kaspersky Lab and AVL Software and Functions GmbH unveiledthe Secure Communication Unit (SCU) at New Mobility World / IAA 2017 in Frankfurt, Germany.
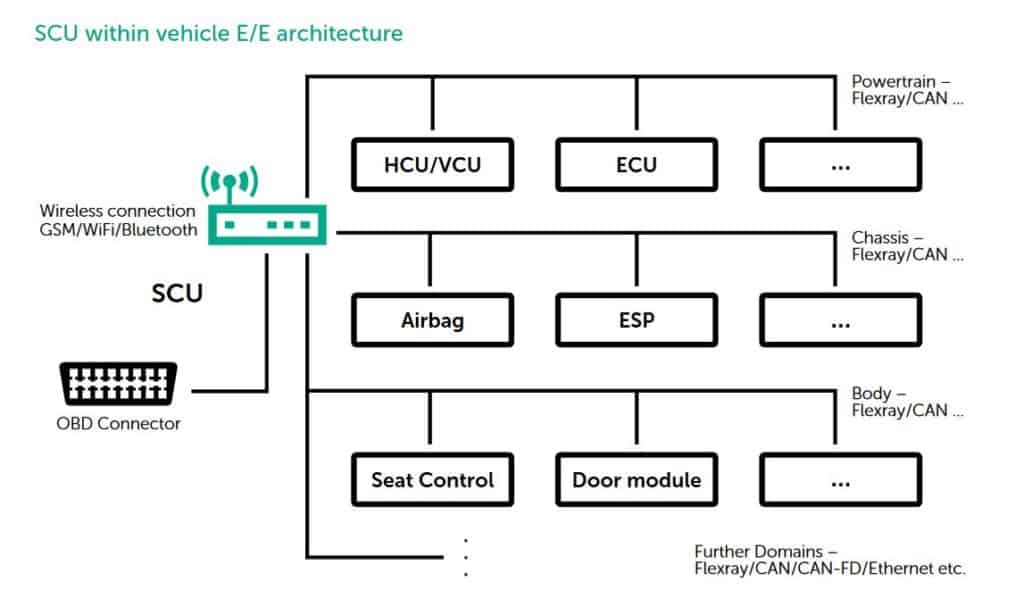 The rising number of third-party applications, system complexity and the increasing dynamic in software update cycles that make use of over-the-air updates has made it difficult to test the complete connected car system for bugs, backdoors and architectural issues. The Secure Communication Unit makes it possible for connected cars to be secure by-design, regardless of the third-party software and systems on board.
The rising number of third-party applications, system complexity and the increasing dynamic in software update cycles that make use of over-the-air updates has made it difficult to test the complete connected car system for bugs, backdoors and architectural issues. The Secure Communication Unit makes it possible for connected cars to be secure by-design, regardless of the third-party software and systems on board.
The SCU is a communication gateway control unit, connected to several subnets and/or gateway-controllers to these subnets within the car network, acting as a single secure gateway for incoming and outgoing communication flows. Based on security policy enforcement and strong separation to prevent unwanted contact between various car components, the software helps ensure proper interference-proof communications within the car network.
The software platform of the SCU consists of security components that are trustworthy-by-design. The microkernel proprietary operating system, KasperskyOS, is based on well-established principles of security-driven development and specifically designed for embedded systems with strict cybersecurity requirements. KasperskyOS removes the chance of undocumented functionality, and thus mitigates the risk of cyberattacks; even if unauthorized code is embedded, it will not be executed because undocumented functionality is prohibited by default. Other components include a security policy engine, Kaspersky Security System, defining the scope and character of interaction between various components and a trusted channel framework with a set of crypto algorithms, as well as low-level protection services based on hardware capabilities.
The SCU prototype presented is exemplarily implemented in ARMv7 architecture with recommended 128 MB RAM and IOMMU. Other hardware platforms can be developed on a case-by-case basis in accordance to the requirements of a particular manufacturer.
The platform provides the solution framework for specific customized applications, allowing car manufacturers to develop and implement unique SCUs into their cars, based on hardware and additional software components aligning with their manufacturing plans. The SCU is available for OEMs, ODMs, system integrators and software developers around the world.
Panasonic Intrusion Protection System
Panasonic’s newly developed systems will ensure safe driving with autonomous and connected cars by detecting the intrusion of attacks and viruses to the vehicle system due to cyber-attacks and discarding and disabling them using the prevention system. They will make it easier to comply with future in-vehicle security legislation. 
The features of the new systems are as follows.
- Detects intrusions of attacks from the Internet at an early stage, and additionally detects intrusions to the in-vehicle network as a second step.
- In addition to the widely used CAN , the systems are also compatible with Ethernet, which is expected to spread in the future as an in-vehicle network, and enables comprehensive detections of intrusions to the entire vehicle.
- By collecting information from multiple vehicles on the cloud, the systems can detect attacks before they are identified as a true security incident.
The system consists of a vehicle-installed “monitoring module” and a “monitoring cloud” that is linked to the monitoring module. The vehicle-installed monitoring module monitors the entire vehicle based on the monitoring rules. By using the company’s newly developed systems, once the attacks that cannot be detected with existing monitoring modules are discovered, the systems can prevent new attacks by updating the monitoring rules from the monitoring cloud. Therefore, it helps to maintain safety even after the vehicle is released on the market. Also, by grasping signs of attacks before they are identified as true security incidents, they are possible to implement countermeasures in advance so that they can minimize the effects of the attacks.
Technical Features:
- 1. In-vehicle device-type host intrusion detection technology: This technology detects intrusions from the Internet, which is an early stage of the attacks, and can be installed and used with Internet connected devices (IVI/TCU*3) In addition to clearly identifying the attacks from the obtainable logs from an OS like Linux and other various security functions, the system can also detect the attacks by combining multiple behavioral information.
- 2. In-vehicle device-type CAN intrusion detection technology: This technology detects intrusions to CAN communication systems, which is a second stage of the attacks, and can be installed and used with CAN connected devices (ECU) There are two types of CAN monitoring usages, which consist of (1) CAN filter that filter unauthorized CAN commands received by the installed ECU, and (2) CAN monitoring that detects unauthorized commands by monitoring all CAN bus systems that are connected by the installed ECU. Unauthorized commands are judged by taking into consideration various conditions of the vehicle, so it is possible to reduce the number of false positive under specific conditions. Detection of unauthorized commands can be made for each single command, resulting is real-time prevention after detection.
- 3. In-vehicle device-type Ethernet intrusion detection technology: This technology detects intrusions to Ethernet communication systems, which is a second stage of the attacks, and can be installed and used with Ethernet connected devices (ECU) There is an Ether filter that filters unauthorized Ether frames that are received or intercepted by the installed ECU (Ethernet Switch ECU, etc.) The system consists of the overlook method, which can lightly determine unauthorized commands by analyzing the frame headers and a detailed method, which has a high-load operation, but can accurately determine unauthorized commands. Flexible detection is possible by combining these methods.
- 4. Cloud-type vehicle intrusion detection technology: This system analyzes a large amount of logs collected from in-vehicle devices of multiple vehicles through machine learning and can be used by placing it in the cloud. As for the usage, in-vehicle network model that has conducted prior learning, will automatically narrow down the logs that may become potential security risks. After that, the attack analysts will analyze only the selected logs. By linking with various in-vehicle device-type intrusion detection technologies, it is possible to grasp signs of attacks before they are identified as true security incidents.
BlackBerry Security Framework
Since Tech Car Award’s nominations were in December before the introductions of BlackBerry’s Jarvis system, which can be nominated for next year’s voting, please be aware that if you vote for BlackBerry it is for the BlackBerry Security Framework introduced in winter 2017. The company announced a recommended framework to harden connected and autonomous vehicles against cyberattacks.
Within this framework, automakers and their supply chains can deploy their technology choices to differentiate.
BlackBerry’s recommendation leverages the company’s proven expertise in security and accounts for industry trends in connectivity and automated driving. The key points, outlined in the whitepaper titled “Cybersecurity for Automobiles: BlackBerry’s 7-Pillar Recommendation,” are summarized below.
-
- Secure the supply chain: Establish a root of trust by ensuring every chip and electronic control unit (ECU) in the automobile can be properly authenticated and loaded with trusted software, irrespective of vendor or manufacturer. Scan all software deployed for compliance to standards and required security posture. Conduct regular evaluations of the supply chain from a vulnerability and penetration testing perspective to ensure they are certified and “approved for delivery.”
- Use trusted components: Create a security architecture that is deeply layered in a defense in depth architecture, with secure hardware, software, and applications.
- Employ isolation and trusted messaging: Use an electronic system architecture that isolates safety critical and non-safety critical ECUs and can also “run-safe” when anomalies are detected. Additionally, ensure all communication between the electronics in the automobile and the external world are trusted and secure. Further, ECU-to-ECU communication needs to be trusted and secure.
- Conduct in-field health checks: Ensure all ECUs have integrated analytics and diagnostics software that can capture events, and are able to log and report the same to a cloud-based tool for further analysis and to initiate preventative actions. Moreover, automakers should confirm that a defined set of metrics can be scanned regularly when the car is in the field, as well as be able to take actions to address issues via secure over-the-air (OTA) software updates.
- Create a rapid incident response network: Share common vulnerabilities and exposures among a network of subscribing enterprises so expert teams can learn from each other and provide advisories and fixes in shorter time frames.
- Use a lifecycle management system: Proactively re-flash a vehicle with secure OTA software updates as soon as an issue is detected. Manage security credentials via active certificate management. Deploy unified endpoint policy management to manage applications downloaded over the lifetime of the car.
- Make safety and security a part of the culture: Ensure every organization involved in supplying auto electronics is trained in functional safety and security best practices to inculcate this culture within the organization.
If you are interested in fresh up-to-date connected car news subscribe to our newsletters. If you want to be notified of winners please subscribe to ACN Tech CARS Winners newsletter.