 TrendMicro’s Forward-looking Threat Research (FTR), Politenco di Milano and Linklayer Labs team consisting of Andrea Palanca, Eric Evenchick, Federico Maggi, and Stefano Zanero identified a vulnerability exploiting a weakness in the CAN protocol that allows an attacker to perform a denial-of-service (DoS) attack.
TrendMicro’s Forward-looking Threat Research (FTR), Politenco di Milano and Linklayer Labs team consisting of Andrea Palanca, Eric Evenchick, Federico Maggi, and Stefano Zanero identified a vulnerability exploiting a weakness in the CAN protocol that allows an attacker to perform a denial-of-service (DoS) attack.
ICS-CERT has notified some affected vendors, primarily auto manufacturers and entities within the healthcare industry, about the report to confirm the vulnerability and to identify mitigations. ICS-CERT is issuing this alert to provide notice of the report and identify baseline mitigations for reducing risks to these and other cybersecurity attacks.
What’s new is that it’s an attack that disables a device (e.g., airbag, parking sensors, active safety systems) connected to the car’s device network in a way that is invisible to state-of-the-art security mechanisms.
The security issue that was leveraged lies in the standard that specifies how the car device network (i.e., CAN) works. Car manufacturers can only mitigate the attack we demonstrated by adopting specific network countermeasures, but cannot eliminate it entirely.
Researchers report to eliminate the risk entirely, an updated CAN standard should be proposed, adopted, and implemented. This whole process would likely require another generation of vehicles.
The hack abuses the network protocol that connects all in-vehicle equipment (e.g., parking sensors, airbag, active safety system) and systems (infotainment), and allows them to communicate. The standard for this network is called a Controller Area Network, or CAN.
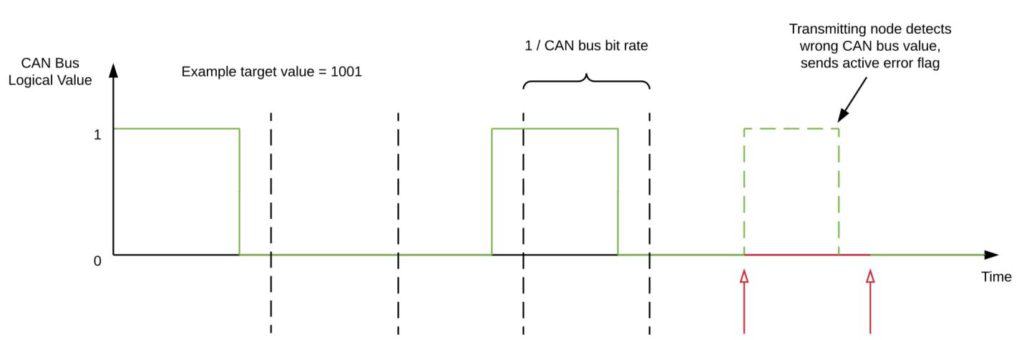
The attack focuses on how CAN handles errors. Errors arise when a device reads values that do not correspond to the original expected value on a frame. When a device detects such an event, it writes an error message onto the CAN bus in order to “recall” the errant frame and notify the other devices to entirely ignore the recalled frame. This mishap is very common and is usually due to natural causes, a transient malfunction, or simply by too many systems and modules trying to send frames through the CAN at the same time.
If a device sends out too many errors, then—as CAN standards dictate—it goes into a so-called Bus Off state, where it is cut off from the CAN and prevented from reading and/or writing any data onto the CAN. This feature is helpful in isolating clearly malfunctioning devices and stops them from triggering the other modules/systems on the CAN.
This is the exact feature is what the attack abuses. The attack triggers this particular feature by inducing enough errors such that a targeted device or system on the CAN is made to go into the Bus Off state, and thus rendered inert/inoperable. This, in turn, can drastically affect the car’s performance to the point that it becomes dangerous and even fatal, especially when essential systems like the airbag system or the antilock braking system are deactivated. All it takes is a specially-crafted attack device, introduced to the car’s CAN through local access, and the reuse of frames already circulating in the CAN rather than injecting new ones (as previous attacks in this manner have done).
Going forward, some long-term solutions can help protect against such exploits:
- Network Segmentation or Topology Alteration: By altering the topology or segmenting a CAN in a vehicle, targeted error-flooding can be stopped from affecting a specific system.
- Regulated OBD-II Diagnostic Port Access: The creation of a special hardware key or password in order to open the case where the port is physically located may protect against illegal and unauthorized devices being introduced to the CAN. The implementation of a software-level authentication in order to allow traffic from and to the port can be considered as well. This would require a change in the regulations.
- Encryption: Encrypting CAN frame ID fields can prevent attackers from identifying CAN frames to target, and thus resulting in a noisier and much more detectable attack pattern.
Although, Karamba Security agrees with Trend Micro that the CAN protocol can be abused, causing it to disable devices on a CAN network, and that IDS systems will not be able to help against such an attack.
However, in order to remotely launch Denial of Service (DoS) CAN attacks, a hacker must compromise an externally-connected electronic control unit (ECU) and interfere with its factory settings. Such interference enables the hackers to start sending CAN messages that generate errors leading to a device DoS.
Instead of changing the legacy CAN protocol in all cars that use it (practically all vehicles), the industry should harden the externally-connected ECUs according to their factory settings, to prevent any unauthorized change to the ECU. Blocking such changes enables the industry to prevent cyberattacks, including the DoS attack that Trend Micro reported on.
US/ICS-CERT and an alert has been issued which states tehe only current recommendation for protecting against this exploit is to limit access to input ports (specifically OBD-II) on automobiles. ICS-CERT is currently coordinating with vendors and security researchers to identify mitigations.
ICS-CERT also provides a control systems recommended practices page on the ICS-CERT web site. Several recommended practices are available for reading or download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.