 Researchers, Ian Foster, Andrew Prudhomme, Karl Koscher, and Stefan Savage at the Department of Computer Science and Engineering, University of California, San Diego have found a way to hack into aftermarket OBD-II dongles.
Researchers, Ian Foster, Andrew Prudhomme, Karl Koscher, and Stefan Savage at the Department of Computer Science and Engineering, University of California, San Diego have found a way to hack into aftermarket OBD-II dongles.
A YouTube video shows that they were able to compromise a Corvette with a telematics control unit (TCU) connected to the OBD-II port, sending brake commands while the car was moving, causing it to stop. They also were able to turn on the windshield wipers. Their paper, presented at WOOT 2015 (Usenix Workshop on Offensive Technolgies), shows how network enabled telematic control units (TCUs) can be used to remotely control automobiles from any distance over SMS or the Internet.
The researchers in their paper state these devices can be discovered, targeted, and compromised by a remote attacker. They show how a compromise allows arbitrary remote control of the vehicle. The authors note that this security problem is particularly challenging because aftermarket equipment cannot be well addressed by automobile manufacturers themselves.
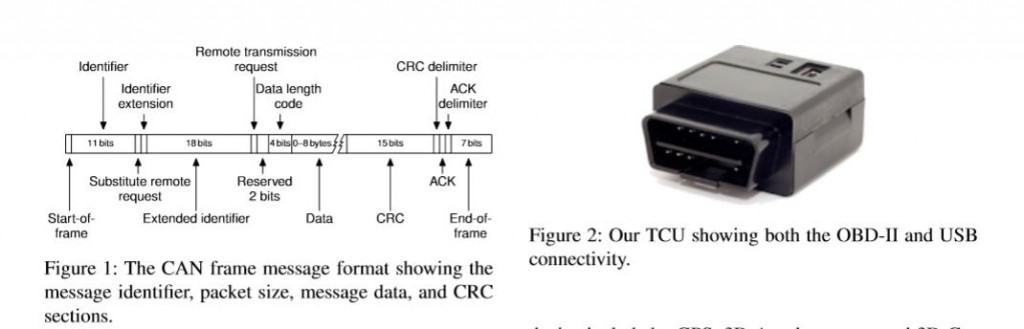
The TCU devices have a microprocessor and a CAN transceiver, as well as GPS, accelerometers and external networking connectivity. Some work with short-distance Bluetooth interface (Automatic Lab’s dongle) and more often there is a full cellular connection for remote data connectivity via the Internet.
The researchers bought a TCU from eBay manufactured by Mobile Devices Ingenierie and known to be used for insurance purposes (Metromile’s per-mile consumer policies and for Uber insurance). Metromile and Uber have both fixed the vulnerabilities via a software update.
The researches demonstrated a remote compromise via SMS. Once compromised, they have shown that the TCU can send arbitrary CAN packets, sufficient to remotely control safety critical automobile features such as the brakes.
Read full paper.
Other hacks in the news recently, include remote hacks of a Jeep Cherokee, OnStar Chevy Volt and Lotus Elise (using a device to intercept the wireless key fob).