 The the darling car hacksters, Charlie Miller and Chris Valasek demonstrated their hacking prowess for Wired on a Jeep Cherokee after FCA released a security patch for the vulnerability.
The the darling car hacksters, Charlie Miller and Chris Valasek demonstrated their hacking prowess for Wired on a Jeep Cherokee after FCA released a security patch for the vulnerability.
Using the zero-day exploit the hackers at a laptop computer 10 miles away, sent commands to the Jeep’s infotainment system.
They were able to control the brakes, radio, windshield wipers, air conditioning, accelerator and brake sending Wired’s contributor, Andy Greenberg into a ditch. Uconnect’s cellular connection allowed them to connect because they knew the car’s IP address of the vehicle.
The hackers discovered a vulnerable element, which Miller and Valasek won’t identify until they speak at the Black Hat hackers conference in Las Vegas on August 1. Last year, at Black Hat they showed their “intrusion prevention device.”
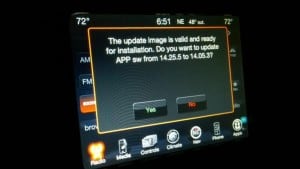
The hacking duo has been working on the hack for quiet some time. On Twitter, in December 2014, Millers reported that, he “bricked” a Jeep Cherokee headunit that had to be replaced. The software the team implanted rewrites the chip’s firmware in the infotainment system to plant their code on other systems.
They informed Chrysler of the vulnerability and the owners can download an update and install it using a USB drive.
FCA says vehicles from the 2013 and 2014 model years with 8.4-inch touchscreen are affected.
The law is trying to catch up to car cyber security threats.
Senators Edward J. Markey (D-Mass.) and Richard Blumenthal (D-Conn.), members of the Commerce, Science and Transportation Committee, today introduced legislation that would direct the National Highway Traffic Safety Administration (NHTSA) and the Federal Trade Commission (FTC) to establish federal standards to secure our cars and protect drivers’ privacy. The Security and Privacy in Your Car (SPY Car) Act also establishes a rating system — or “cyber dashboard”— that informs consumers about how well the vehicle protects drivers’ security and privacy beyond those minimum standards.
NHTSA, in consultation with the FTC, should develop standards that prevent hacking into our vehicle controls systems. These performance standards should require that:
Hacking protection: all access points in the car should be equipped with reasonable measures to protect against hacking attacks, including isolation of critical software systems and evaluated using best security practices, such as penetration testing.
Data security: all collected information should be secured to prevent unwanted access—while stored on-board, in transit, and stored off-board.
Hacking mitigation: the vehicle should be equipped with technology that can detect, report and stop hacking attempts in real-time.
The FTC, in consultation with NHTSA, should develop privacy standards on the data collected by our vehicles. These standards should require.
Transparency: owners are made explicitly aware of collection, transmission, retention, and use of driving data.
Consumer choice: owners are able to opt out of data collection and retention without losing access to key navigation or other features (when technically feasible), except for in the case of electronic data recorders or other safety or regulatory systems.
Marketing prohibition: personal driving information may not be used for advertising or marketing purposes without the owner clearly opting in.
Argus cyber solutions claims it could have successfully prevented such attacks from affecting a vehicle’s systems.